With each wave of ransomware attacks, and major vulnerability announcements from popular 3rd party systems, we see IT Managers reaching out for support to secure Schoolbox.
For our managed cloud services the Schoolbox team handles these issues as part of the service, one of the added benefits of moving to cloud hosting.
For our Schoolbox on-premise community, we understand ensuring Schoolbox data is protected and your server remains healthy is an ongoing challenge and incredibly important. To get you started this article discusses some of the basic steps you need to take.
Network Security
The first and most important step is to minimise the attack surface, for on-premise installations this is done by setting up Schoolbox inside an appropriate DMZ firewall.
The DMZ will prevent inappropriate traffic from both entering and leaving the Schoolbox server. Ideally Schoolbox will be isolated in the DMZ from other servers to prevent any lateral movement if a compromise were to occur.
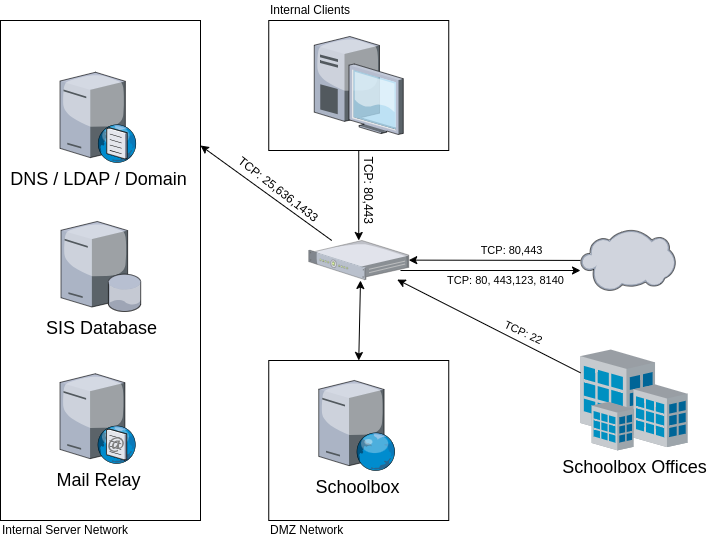
Schoolbox relies on common network services like Mail, DNS, LDAP and NTP in order to function, but we do not require any additional access to your network. If your email service is cloud hosted, you should adjust your firewall appropriately.
We frequently get asked about closing port 80 to prevent insecure HTTP traffic. This port is vital to validate LetsEncrypt SSL certificates and redirect clients who attempt to load the traditional HTTP URL. We still ensure all user traffic will always be encrypted.
Our remote access is critical to ensure Schoolbox timely support and management. But that access should be limited to the Schoolbox office IP addresses. This ensures that only authorised Schoolbox employees can access the server.
Investing in solutions that will make a difference to network security is just as important as choosing not to pursue solutions that don’t provide additional security value. This is one of the conversations we have with customers who are looking to place a reverse HTTP proxy in front of Schoolbox. This solution can be challenging because of the large number of systems and the difficulty in configuring them, combined with their limited support for web sockets. Most importantly, this solution does not provide any additional security over and above our recommended practice.
Support Desk Security
One of the common areas of security that can be overlooked is the support desk. At Schoolbox we ensure our support agents are all vetted and appropriately trained. With critical access to many systems, each time a support agent accesses your system this is logged and reported.
We also try to minimise the sharing of certificates and passwords via our support desk, but if we must, this is done using one time keys. We now recommend using LetsEncrypt as it minimises the handling of private keys.
Of course our agents will only initiate changes, upgrades or share data with your registered support people.
Backups
Although not directly a security issue, in the advent of a security incident we all know the first thing that you look at is your backup. These can be important for both forensic purposes and also getting back to a known healthy state. It is important that you maintain both fast to recover backups, and also slower air gapped systems. In many recent ransomware attacks backups were impacted, so it is important that security is considered when implementing a backup solution.
Monitoring and Agents
At Schoolbox we monitor our entire fleet using a range of diagnostic tools. This allows us to keep a track of everything happening across our growing fleet.
We monitor performance metrics and logs utilising Grafana. All data is collated centrally allowing us to identify servers under stress, trends across the fleet, service availability and security issues.
At the product level we log all errors experienced by users. This allows us to proactively fix and view the impact of bugs in the system. We also send usage metrics to a central database where we can graph usage and engagement for each feature across the platform.
We understand sometimes customers wish to supplement our monitoring with their own, although we permit installation of these agents on the Schoolbox server, they come with their own risks. 3rd party agents are not supported by Schoolbox as we cannot guarantee their impact on performance or if they could reduce server security. We are also unable to provide support in the event that they do not function correctly.
A simpler solution Schoolbox can provide is to utilise the existing SNMP server, and collect metrics via SNMP. This service can sometimes be identified in security audits so if you choose to utilise this you should ensure it is firewalled appropriately. In the future we hope to extend this to allow system logs to be forwarded to 3rd party systems as well.
Deploying Updates
Keeping the system up to date and patched is critical to the security of any system. This is a shared responsibility between Schoolbox and your teams as some updates are only available on demand. So although we do our best to keep everything up to date, we need your help to schedule appropriate upgrades and keep things running smoothly.
In order to ensure the correct software packages and updates are applied we utilise Puppet. We constantly monitor for updates to packages, security announcements and changes that could affect our fleet.
- Standard operating system packages are updated automatically every week.
- Important updates to mission critical systems are first deployed to staging for testing and then promoted to production.
The upgrade process can vary depending on how critical the update is and how much disruption it may cause. This also means the process could take a single day or can be several weeks in some instances.
If we identify any major security issues with the potential to be exploited we immediately report to all customers. This includes issues discovered in the underlying systems that support Schoolbox, along with the product code itself.
Penetration Testing
Security is a part of our everyday practice at Schoolbox, with code reviews, security testing and frequent dependency audits. But sometimes you need a second pair of eyes to discover those unexpected vulnerabilities.
We welcome all independent security reviews conducted by you, your security contractors or even your students. We treat all vulnerability disclosures and penetration test reports with the highest priority and will work to remediate any reported issues as quickly as possible.
If you are conducting penetration testing we recommend that you complete it against your staging server. Some automated test tools have been known to damage production data, so please be careful and ensure that any automated testing is conducted safely.
User Authentication
Phishing attacks are the most common form of compromise, these attacks target a user’s authentication credentials.
To ensure only valid users are accessing your system we recommend implementing SAML authentication using a modern identity management system. Ideally this system should provide multi-factor authentication, beyond just a password and it should feature brute force detection and account lockouts in the event of many failed attempts.
In addition to SAML we also support oAuth for mobile devices, removing the need for LDAP authentication. However if you must use LDAP, ensure it is LDAPS and you have the required certificates installed on your server.
Of course it goes without saying that users should be encouraged to practice good password hygiene, including being able to regularly change their passwords and set long, but easy to remember passwords.
Managing Permissions
The last line of security is in app access permissions. Ensuring users only have access to what they need is an important step to limiting damage, either accidental or deliberate. To this end, keeping a limit on the number of super user accounts is very important. We recommend you frequently audit your users for privileges and access, disabling users and removing super users as required.
Schoolbox sees security as a partnership. In an increasingly hostile environment, with an ever increasing amount of sensitive PII information, the best security is achieved when we work together closely, monitor each other and provide defense in depth across all the possible layers.
Additional Resources